Cyber security is one of the main issues that organizations are struggling with every day. In fact, according to Accenture, 68% of business leaders say their cybersecurity risks are increasing. Therefore, it is critical to understand the various facets of cybersecurity, and this includes the cyber kill chain.
Ignoring cybersecurity is proving to be one of the costliest mistakes. After all, this decision led to a 72% increase in the average cost of cybercrime over the last 5 years. However, with cybersecurity, it is not possible to completely eliminate risks. Therefore, having defense strategies in place can be the best possible solution to mitigate cybersecurity risk.
By using a layered security approach, risks can be minimized. However, how do you ensure that your cybersecurity system is strong enough to withstand any attack on your organization? This is where the cyber kill chain has a role to play.
In this article, we will discover what a cyber kill chain is and how companies can use it to protect themselves from attacks.
What is a cyber kill chain?
The cyber kill chain is essentially a cybersecurity model created by Lockheed Martin. Its aim is:
- track the stages of a cyber-attack;
- identify vulnerabilities;
- help security teams stop attacks at every step of the chain.
The term cyber kill chain is adopted by the military, who use this term related to the structure of an attack. After all, it consists of identifying a target, dispatching, deciding, ordering, and, finally, destroying the target.
How does the cyber kill chain work?
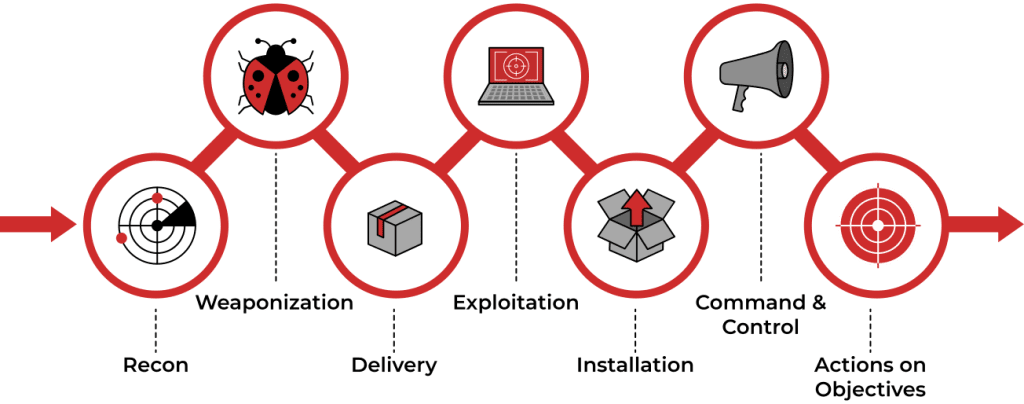
The cyber kill chain consists of 7 distinct steps:
-
Recognition
The attacker collects data about the target and tactics for the attack. This includes collecting email addresses and collecting other information.
Then, automated scanners are used by attackers to find points of vulnerability in the system. This includes checking firewalls, intrusion prevention systems, etc. to gain an entry point for the attack.
-
Armament
Attackers develop malware by taking advantage of specific security vulnerabilities. Then, they design the malware based on their needs and the intent of the attack. This process also involves attackers trying to reduce the chances of being detected by the security solutions the organization has in place.
-
Delivery
The attacker delivers the weaponized malware via a phishing email or some other means. The most common delivery vectors for weaponized payloads include websites, removable disks, and emails. This is the most important stage where the attack can be stopped by security teams.
-
Exploration
The malicious code is delivered to the organization’s system. So, it is at this stage that the perimeter is breached. Then, attackers have the opportunity to exploit the organization’s systems by installing tools, running scripts, and modifying security certificates.
Most of the time, vulnerabilities in an application or operating system are targeted. Examples of exploit attacks can be scripting, dynamic data exchange, and local task scheduling.
-
Installation
A backdoor or remote access trojan is installed by the malware. This, in turn, provides access to the intruder. This is also another important step where the attack can be stopped using systems like HIPS (Host-based Intrusion Prevention System).
-
Command and Control
The attacker gains control over the organization’s systems and network. That is, attackers gain access to privileged accounts and attempt brute-force attacks. However, they also search credentials and change permissions to take control.
-
Actions on the Objective
The attacker finally extracts the data from the system. After all, its objective involves collecting, encrypting, and extracting confidential information from the organization’s environment.
Based on these steps, the following control implementation layers are provided:
- Detect – Determine penetration attempts within an organization.
- Deny – Stop attacks when they are happening.
- Interrupt – Intervene in the data communication made by the attacker and then interrupt it.
- Degrade – This is to limit the effectiveness of a cybersecurity attack in order to minimize its harmful effects.
- Deceive – Deceive the attacker by providing wrong information or misdirecting them.
- Contain – Contain and limit the scope of the attack so that it is restricted to only one part of the organization.
Recognition
- Detect: Web Analytics; Threat Intelligence; Network Intrusion Detection System
- Deny: Information Sharing Policy; Firewall Access Control Lists
Armament
- Detect Threat Intelligence; Network Intrusion Detection System
- Deny: Network Intrusion Prevention System
Delivery
- Detect: endpoint malware protection
- Deny: Change Management; App whitelist; Proxy filter; Host-Based Intrusion Prevention System
- Stop: Built-in Antivirus
- Downgrade: Row
- Contains: Router Access Control Lists; Application-aware firewall; Trust Zones; Cross-Zone Network Intrusion Detection System
Exploration
- Detect: Endpoint malware protection; Host-Based Intrusion Detection System
- Deny: Secure Password; Patch management
- Stop: Data Execution Prevention
- Contains: Application-aware firewall; Trust Zones; Cross-Zone Network Intrusion Detection System
Installation
- Detect Security Information and Event Management (SIEM); Host-Based Intrusion Detection System
- Deny: Separation of Privileges; Strong passwords; Two-factor authentication
- Stop: Router Access Control Lists
- Contains: Application-aware firewall; Trust Zones; Cross-Zone Network Intrusion Detection System
Command and control
- Detect: Network Intrusion Detection System; Host-Based Intrusion Detection System
- Deny: Firewall Access Control Lists; Network segmentation
- Disrupt: Host-Based Intrusion Prevention System
- Downgrade: Tarpit
Cheating: Domain Name System Redirection
- Contains: Trust Zones; Domain name system sinkholes
Actions on Objectives
- Detect: endpoint malware protection
- Deny: data encryption at rest
- Disrupt: Endpoint Malware Protection
- Degrade: Quality of Service
- Cheat: Honeypot
- Contain: Incident Response
Exfiltration
- Detect Data loss prevention; Security Information and Event Management (SIEM)
- Deny: output filtering
- Stop: Data Loss Prevention
- Contains: Firewall Access Control Lists”
How can a cyber kill chain protect against attacks?
A cyber kill chain or cyber attack simulation platform can be used by organizations to identify and fix security flaws in their system within seconds.
So, here’s how simulating a cyber kill chain can protect against cybersecurity attacks:
-
Simulate cybersecurity attacks
Real cybersecurity attacks can be simulated across all vectors to find vulnerabilities and threats. This includes simulating cyber attacks through email gateways, web gateways, web application firewalls, and the like.
-
Assess controls to identify security gaps
This involves evaluating simulations and identifying areas of risk. Simulation platforms provide a detailed risk score and report on all vectors.
-
Remediate and fix cybersecurity gaps
The next step is to fix the security gaps that were identified in the previous step. This may include steps such as installing patches and changing settings to reduce the number of threats and vulnerabilities on the organization’s system.
Final thoughts
Different security techniques present different approaches to the cyber kill chain. After all, everyone from Gartner to Lockheed Martin defines stages slightly differently. However, alternative models of the cyber kill chain combine several of the above steps into a C&C (command and control, or C2) stage and others into an ‘Actions on Target’ stage. Some combine lateral movement and privilege escalation into an exploration stage; others combine intrusion and exploitation in an “entry point” stage.
However, this is a model that is often criticized for focusing on perimeter security and limited to malware prevention. However, when combined with advanced analytics and predictive modeling, the Cyber Kill Chain becomes critical to data security.
With the above breakdown, the cyber kill chain is structured to reveal the active state of a data breach. However, it is important to highlight that each stage of the kill chain requires specific instrumentation to detect cyber attacks.
On the other hand, leaving cybersecurity vulnerabilities open for security attacks is one of the most common mistakes made by organizations today. Therefore, continuous security validation across the Cyber Kill Chain can help companies identify, prevent, stop, and prepare for these attacks.
Need help with security?
You can hire an IT company to take care of your cybersecurity and much more.