Cyber threat intelligence and monitoring are critical to stopping a modern cyber attack. Still, many organizations don’t have the staff, expertise, or budget to collect, process, and analyze the information needed to stop attacks. Without access to the most up-to-date cyber threat intelligence, your organization is more likely to be attacked.
This article discusses cyber threat intelligence, how intelligence is developed, the types of intelligence available to different audiences, and the alternatives available to any organization that cannot afford an in-house cyber threat intelligence program.
“Threat intelligence” is evidence-based knowledge, including context, mechanisms, indicators, implications, and actionable advice, about an existing or emerging threat or hazard to assets, which can be used to inform decisions regarding the subject’s response to that threat or hazard.” – Gartner
Cyber threat intelligence (CTI) is actionable data collected and used by an organization’s cybersecurity systems and/or security experts to help them better understand vulnerabilities, take appropriate action to stop an attack and protect the company’s network and endpoints from future attacks. The data includes information such as who the attacker is and what their capabilities, motivations, and attack plans are.
Cyber threat monitoring is a solution that uses strategic intelligence to continuously analyze, assess, and monitor an organization’s networks and endpoints for evidence of security threats, such as network intrusion, ransomware, and other malware attacks. Once a threat is identified, threat monitoring software issues an alert and stops it.
Why is cyber threat intelligence important?
You cannot reliably stop any cyberattack without a detailed threat report. In the age of remote work, where employees use bring-your-own-device (BYOD) and unprotected networks, cyber threat intelligence is more important than ever. With cyber threat intelligence and monitoring, an organization has the strongest data protection and information needed to stop or mitigate cyberattacks. Cyber threat intelligence (CTI) provides:
- Information about the data, including context, to help prevent and detect attacks.
- Prioritized alerts that help you respond faster to incidents.
- Improved communication, planning, and investment by identifying real risks to the business.
Who can benefit from cyber threat intelligence?
Organizations large and small, governments, and nation-states can benefit from cyber threat intelligence (CTI). Yet few organizations have analysts on staff working with the volume of information and making decisions about what data is valid and what threats are real.
Experts have estimated that it would take 8,774 analysts working full-time for a year to process the same amount of security event data that Machine Learning (ML) can process in the same amount of time.
This is why many organizations turn to Artificial Intelligence (AI) and machine learning to analyze tactical and operational threat intelligence needed for timely detection and incident response to satisfy a sound security posture.
Cyber Threat Intelligence Life Cycle and Process:
Industry experts say there are five or six iterative process steps in the cyber threat intelligence lifecycle that turn raw data into intelligence. The CIA first developed a six-step lifecycle process, while other security experts have combined and condensed the five-step lifecycle process as follows:
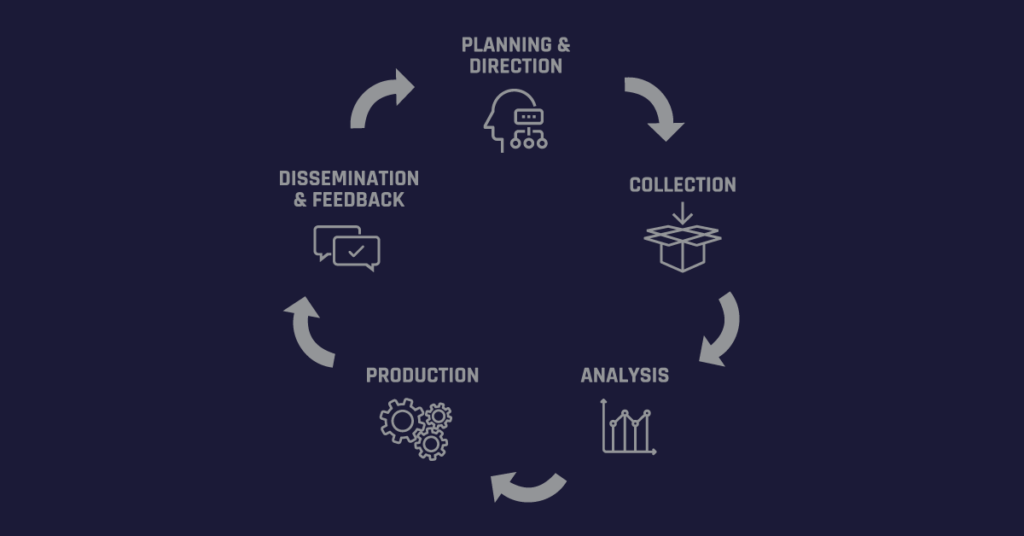
Cyber Threat Intelligence Life Cycle: Planning, Collection, Processing, Analysis, Dissemination
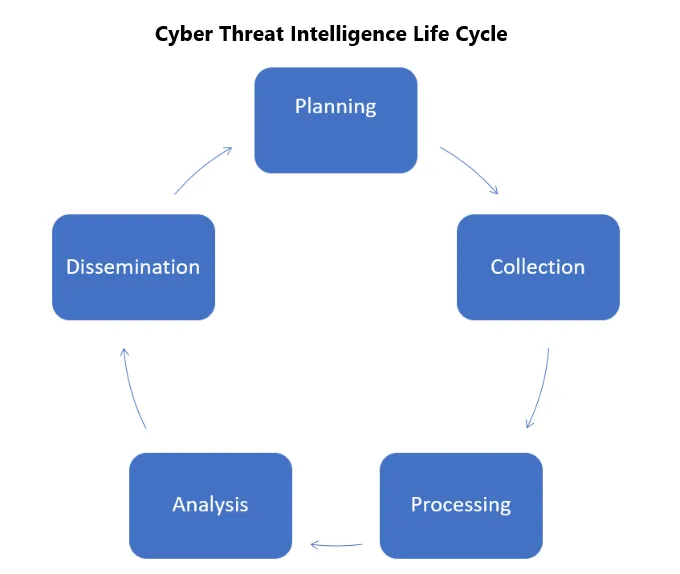
1. Planning and direction. In this phase, the Chief Information Security Officer or Chief Security Officer establishes the goals and objectives of the cyber threat intelligence program. This includes identifying sensitive information and business processes that need to be protected, the security operations needed to protect data and business processes, and prioritizing what to protect.
2. Collection. Data is collected from multiple sources including open-source sources, internal threat intelligence, vertical communities, business services, and dark web intelligence.
3. Processing. The collected data is then processed into a suitable format for further analysis.
4. Analysis. In this step, data is combined from different sources and transformed into actionable intelligence so that analysts can identify patterns and make informed decisions.
5. Diffusion. Threat data analysis is properly published and disseminated to business stakeholders or customers.
We refer to the process as a “cyber threat intelligence cycle” because addressing digital attacks is not a single process, but rather a circular process that takes each cyber experience and applies it to the next.
What is cyber threat modeling?
Cyber threat modeling is a practice designed to optimize network security. It does this by locating system vulnerabilities, identifying clear targets, and developing a strategy to counter the potential effects of cyberattacks against an application or computer system.
While it can be run at any stage of development, it is most fruitful if it is done at the start of a project. The logic is this: the sooner you identify new vulnerabilities, the easier it is to deal with them. On the other hand, if weaknesses remain unattended, they can become serious security problems in the future.
The approach allows your IT team to dig deeper into potential dangers to your system and how they might affect your network. Cybersecurity professionals can use the practice to harden all potential entry points, enforce application security in line with potential weaknesses, and protect Internet of Things environments.
The threat modeling procedure depends on the system being examined. However, any organization dependent on technology can benefit from it. Threat modeling allows security professionals to narrow down particular hits targeting a specific system.
This eliminates potential confusion and allows teams to focus only on those that can impact their business. Packed with such knowledge, your security team could defend your company’s system long before an attack hits it.
However, threat modeling requires a thorough process to optimize your cyber defenses to the teeth. In the next section, we’ll discuss the steps needed to make threat modeling more beneficial to your business. All of them can “act” individually since they are independent processes. However, running together provides the most comprehensive view of any potentially harmful scenario.
Let’s go over the steps now.
Steps for Comprehensive Threat Modeling:
The steps for robust threat modeling can be simplified to preparation, analysis, implementation, and review. However, they all depend on a series of questions to function optimally.
Below is a list of questions threat hunters should ask before finalizing a final threat model.
· Which threat models are most suitable for your company?
Answering this question requires inspecting data flow transitions, data classifications, and architecture diagrams to arrive at a virtual network model that needs protection.
· What are the drawbacks?
For this, you must investigate the main threats to your network and applications.
What to do in the event of a possible cyberattack?
For this question, you would need to identify the best way to counter specific vulnerability issues and scenarios in which threat actors exploit those vulnerabilities.
· How does the threat model work?
Companies must monitor counterattack processes to determine their quality, efficiency, and feasibility. Conducting a comprehensive model performance review could catalyze a better planning process and speed up your progress.
To include the questions in a list of steps, you can refer to the list below.
- Describe the security concerns of a specific system, application, or process.
- Make a list of suggestions for potential threats to check for as conditions change over time.
- Make a concrete list of threats.
- Make a list of remediation and removal actions.
- Monitor and rate the methods in use to determine their success rate and validity as threats evolve.
Now that you’re familiar with the basics of threat modeling, let’s review the threat modeling process in a bit more depth.
The Threat Modeling Process:
As we’ve mentioned, threat modeling can define an organization’s assets, identify the role of applications in the big picture, and contain a security profile for specific applications.
The process proceeds to identify and prioritize potential threats. Security professionals can then use the collected data (and conclusions) to classify potentially harmful events and determine what actions could be taken to resolve the issues.
In essence, threat modeling is taking a step back to access a company’s digital and network assets, identify external and internal threats, determine existing malicious indicators, and devise a plan to protect against them (or to recover sensitive information from them). securely if a threat manages to penetrate the company’s defenses).
In the same way that a “kill chain” describes the structure of an attack in the military, you can create a cyber kill chain to understand how attackers think and counter them proactively.
Below, we’ll break down the threat modeling process into additional steps to make it easier for you to follow through.
Keep in mind that each individual process is unique depending on the network, company preferences, and issues that arise. However, the basic approach remains somewhat concrete.
1. Create a secure design, network model, or application defense system.
2. Make sure that resources are spent in the most efficient way possible to avoid unnecessary expenses (either in the form of more money or more people assigned to do a task).
3. Make security a priority. In most cases, strong security outweighs short-term profitability, as a security system will bring more profit in the long term (and effectively protect it while it is operational).
4. Inform stakeholders about system development.
5. Specify all potential system threats.
6. Identify compliance requirements based on the specific system or application being addressed.
7. Ensure that all measures taken comply with the necessary regulations.
8. Define the controls needed to counter cybercriminals before, during, and after potential attacks.
9. Build such controls and present them transparently to all stakeholders.
10. Assess all risks related to the threat management system.
11. Document impact threats to the system.
12. Document mitigation efforts applied to counter various threats.
13. Ensure that business objectives are not affected by malicious actors or adverse events.
14. Test the system to ensure its operability against indicators of compromise to protect your company’s network.
15. Build on the foundation you’ve created until you have a comprehensive security plan for your specific use case.
Advantages of threat modeling to mitigate the effect of cyber threats:
As challenging as threat modeling may seem, it significantly benefits companies that implement it correctly.
For example, the approach can provide a holistic view of software projects and point out the security measures needed to protect the data in those projects. With it, you can document known security threats (for the application) and take the necessary actions to address them appropriately.
Otherwise, if your IT teams act on instinct without supporting evidence, they may not be able to make optimal decisions regarding the security of your data.
Well-designed threat models can ensure that an application on your network is protected against all known cyber threats. Additionally, realistic threat modeling may prove to be the most efficient way to accomplish a list of practical tasks for your business.
Let’s see them below.
- · Detect problems in the Software Development Life Cycle (SDLC) before any coding work has begun.
- · Identify slippery design flaws that would be undetectable by traditional code reviews and testing methods.
- · Assess a broad list of threats that you might otherwise overlook.
- · Optimize test budgets.
- · Identify data protection and security requirements.
- · Remediate software issues prior to application release, thus avoiding additional costs spent for recoding after deployment.
- · Consider exotic threats specific to the unique nature of your application.
- · Maintain a clear vision of possible external and internal threats to the specific application.
- · Identify assets, vulnerabilities, malicious agents, and the controls needed to optimize application components (to reduce the potential attack surface for malicious individuals).
- · Calculate and establish potential hacker location, skills, motivations, and capabilities to understand and locate potential cyberattacks targeting your system architecture.
Misconceptions about the cybersecurity aspects of threat modeling
The term “threat modeling” raises several misconceptions for many users. Some of them perceive that the approach can only be applied when designing an application. Others consider it an optional task, easily substituted for code review and penetration testing. There are also companies that see the process simply as too complicated and redundant an activity.
Below, we will examine these misconceptions to give you a better idea.
- · Code review and penetration testing are not substitutes for threat modeling
Code review and penetration testing are effective when bugs are found in the code. They are a fundamental part of any application development process. However, with threat modeling, you can initiate dedicated security assessments and uncover complex design flaws that, if left unaddressed, can lead to security breaches.
Threat modeling can also be done post-deployment:
As we have mentioned, it is best to start threat modeling early in the design stage. However, that doesn’t mean you shouldn’t resort to the post-deployment approach.
As an application becomes more accessible after deployment, new cyber threats may emerge. Without an assessment of all current threats to an application, you cannot protect it against all potential risks. By monitoring weaknesses in the post-deployment stage, you enable faster and more effective remediation for the application.
- · Threat modeling is not a complicated process if approached sensibly
Many developers find threat modeling challenging. The process seems slow and tedious when examined before a plan has been established. However, you can break it down into doable tasks categorized into systematic steps.
Each task follows the previous one, so as long as you follow the “script”, you can perform threat modeling without much hassle. Be it regarding a simple web application or a complex architecture.
Threat Modeling Techniques for Security Teams:
Decomposition is a fundamental part of the threat modeling process. Here, the term refers to taking an application or infrastructure, breaking it down into elements, and then taking each element to inspect it against possible weaknesses.
By decomposing, you can understand how an application works and interacts with all the entities in the system. Additionally, you can determine which entities may pose cybersecurity threats or invoke problems for the application.
To perform a decomposition process, you need to study the behavior of the application (or system) in the context of as many different scenarios as possible. These cases may include:
- · How does the application behave for users with different levels of access?
- · How does it behave while connected to various network architectures?
- · How does the system process different types of data?
After answering the questions above, you should have a full list of potential entry points and pain points, and more importantly, understand how these change depending on a specific interaction.
To facilitate their work process, IT teams must rely on diagrams that describe the flow of data. This way, they can see a visual representation of data movement in, through, and out of a system (or an application).
Diagrams could also show how data changes at different stages of processing or storage. Finally, diagrams show where specific data is stored as it moves through the system.
Data flow diagrams also allow teams to identify confidence boundaries. Essentially, teams need to be able to determine the points at which data needs to be validated before it can be allowed to enter a specific entity (which will use that data to perform tasks).
Data must be able to flow wherever it needs to be processed (on-premises servers, the cloud, secondary location storage).
Regardless of the destination, the data will enter different networks. Data flow diagrams must describe the precise moment when sensitive information crosses from one network to another.
Once intersection points have been established, your teams can set confidence boundaries at particular locations. This will alert security protocols to enact protection procedures to protect the network against malicious code, should a hacker attempt to penetrate your defenses.
Threat modeling approaches:
Now that you’re familiar with the basic practices, let’s explore specific approaches to the process.
The first methodology on the list is developed by Microsoft and helps IT teams identify system weaknesses in six categories.
Impersonation – When an attacker impersonates a different user, component, or other system feature that contains an identity on the target system.
Tampering: alteration of data within an application or a system to enable malicious actions.
Disavowal: When an intruder denies malicious activity due to insufficient proof of their actions.
Information Disclosure: The exposure of protected data to unauthorized users.
Denial of Service: When an attacker uses illegitimate means to exhaust or deny services necessary to provide service to users.
Elevation of Privilege: When an intruder executes commands and functions that they should not have permission to do.
Harm Potential, Reproducibility, Exploitability, Affected Users, Discovery (DREAD):
Microsoft abandoned this approach in 2008 due to inconsistencies found. However, many other organizations currently use it. In essence, it allows for the classification and management of risks into five categories.
Damage Potential – Ranking the extent of damage made possible by an exploited weakness.
Reproducibility: classify the complexity required to reproduce an attack.
Exploitability: assigning a numerical rating to the efforts required to launch a malicious attack.
Affected Users – Return a value to calculate how many users would be affected if an exploit were widely available.
Discovery: measure the ease of discovering a specific exploit.
What are the six steps of threat modeling?
Threat modeling can be divided into two main processes: discovery and implementation.
These processes can be divided into three threads each.
Discovery:
This is the process in which cybersecurity professionals identify critical infrastructure and the issues surrounding it.
They also use tactical intelligence to determine possible paths that hackers can use to try to infiltrate.
· Implementation:
This process is based on the strategic intelligence gathered in the discovery phase. Cybersecurity professionals can analyze the data to determine organizational and repetitive impact, prioritize the most damaging attacks, and calculate the steps required to harden assets along with prioritized attack paths.
Discovery:
The discovery phase comprises three crucial steps: locating the most sensitive information assets and prioritizing them to perform a comprehensive risk assessment regarding your digital environment.
1. Identification of assets
First, you must catalog all of the company’s assets; these include data, applications, network components, etc. You can divide assets into two main categories.
2· Data assets
Data assets include data, components, and functions that hackers can use to break into your system. For example, hackers can mine various data assets to “help” their crypto mining operations or harvest customer data to sell on the dark web.
i· Commercial assets
Here, you will place data, components, and applications vital to the ongoing operations of your organization. Cybercriminals targeting your company assets could be linked to ongoing sabotage campaigns to disrupt your business.
Some assets would fall into both categories. For them, the best practice is to exhaustively catalog them rather than strictly define them.
ii. Analysis of the attack surface
Most modern hackers won’t go to the trouble of customizing attacks to target their business. You may view them as opportunists locked into the most direct entry points of any system. Its main goal is to exploit known vulnerabilities to compromise or steal sensitive data.
The main vulnerabilities within most enterprises are compromised hardware, software, and unprotected administrator accounts (those still equipped with their default passwords).
Hackers can go through all three entry points until they find an exploit and carry out an attack.
To counteract this, companies need to map the environmental components surrounding the aforementioned assets. Note that the process includes not only core components but also those with access to them (either communication or containment).
Once the map is complete, you will have a complete plan of your attack surface. The attack surface comprises the exposed components that allow a malicious actor to access your assets.
Security specialists must describe all the elements on the attack surface, calculate the data flow, and demonstrate how an attacker can penetrate through one (or more) of the components.
3. Attack vector analysis
The attack surface refers to the plane of the components related to the exposed assets. Attack vectors are the different paths criminals can take to reach one of the plane’s weak points.
You must map all components and their available functionality to include security applications and controls. Typically, hackers could use multiple ways to exploit a specific route.
You then need to collect all the relevant data regarding the known exploits corresponding to each listed component.
Now that you have all the information, you have to try to think like a hacker. It is up to your security teams to outline the hacker’s approach to launching an attack based on the information gathered about the weak points. Here, consider everything you can think of your goals, motivations, hacking skill levels, ability to monetize your efforts, etc.
Once this is done, you should be able to assess how a potential hacker may attempt to infiltrate your systems.
i.Implementation:
Having all of the discovery data is nice and all, but it needs to undergo extensive analysis to benefit you the most. First, you’ll need to break down the impact of each attack vector, then prioritize its potential effects across the enterprise, and finally create a comprehensive list of vulnerability mitigation guidance for each potential issue.
4. Thorough analysis
Risk assessment and risk management are the cornerstones of cybersecurity best practices for this step. They allow you to ensure that you are taking the best possible steps to mitigate risks and secure your resources.
Here, you can use all the data from the discovery to assess the expected impact of each attack. It is best to include any inferences made in the discovery phase and all threat intelligence and indicators of compromise.
Because cyberattacks often trigger a chain of events, it’s critical to review all potential milestones and determine the various ways an attack could harm your business. You can follow the list below to facilitate your analysis phase:
- Data breaches resulting in leaked data regarding all parties involved
- Better costs to replace any compromised equipment
- Damage to your company’s reputation among consumers and competitors
- Any legal action was taken due to a successful attack
- General business downtime after sabotaging of crucial components
5. Prioritization:
As you’ve probably noticed, each step builds on the previous one to gather information to improve your critical security strategy.
In step 5, your goal is to prioritize all previously discovered pain points. Since it’s nearly impossible to eliminate risk from all potential threats, your cybersecurity specialists need to focus on protecting against the most fearsome and high-impact threats.
Understanding the potential occurrence of a high-impact attack is a fundamental part of any risk management process. However, the calculation of the impact of such attacks exceeds their potential occurrence.
By following best practices, you could mitigate most (or all?!) of the critical exploits and counter as many additional issues as possible, depending on their position on your impact assessment list.
6. Application of security controls:
The last step revolves around security checks. Such controls must effectively counter, eliminate or mitigate all exposed vulnerabilities.
Here it is essential to analyze existing security operations to enforce continuous improvements. By doing so, you can identify additional security gaps that were missed in the initial discovery phase.
Lastly, a complete security model should be viewed as a living element of your infrastructure. Even after you’ve gone through all the build steps, it’s crucial to monitor performance and apply security validation to ensure the continued security of your assets.
What are the five threat levels for potential cyberattacks?
Threat levels are designed to indicate the probability of a cyber attack. They go as follows:
1. Low: A cyberattack is highly unlikely to occur
2. Moderate: a cyberattack is possible but not likely to occur
3. Substantial: a cyber attack is likely to occur
4. Serious: a cyberattack is very likely to occur
5. Critical: An attack is very likely to occur in the near future
Types of cyber threat intelligence and monitoring:
Depending on the requirements and the audience, there are three categories or types of cyber threat intelligence.
What is strategic cyber threat intelligence?
Strategic cyber threat intelligence is developed for executive and/or board-level review. It includes non-technical intelligence reports that discuss the trends, risks, and consequences of a cyberattack so that the reader understands the impact on business decisions. The approach is typically generated on demand, and the information can take the form of a report, white paper, policy document, or industry publication.
What is tactical cyber threat intelligence?
Security advocates and decision-makers use tactical threat data to help them understand the latest attack vectors and techniques. By continually understanding the latest attack approach and methods, an organization can develop better defense strategies and allocate security resources.
What is operational cyber threat intelligence?
Operational intelligence provides specific information to help incident response teams stop an attack by better understanding the nature of the attack, the attack method, and its timing. A modern cybersecurity solution using machine learning (ML) is the best method for developing operational cyber threat intelligence.