An organization’s DNS systems can be a gateway for intruders looking to exfiltrate sensitive data without raising alarms. Knowing what’s at stake and how to protect against DNS tunneling can stop attacks before they start.
What is DNS?
DNS stands for Domain Name System and is a service that translates domain names into corresponding IP (Internet Protocol) addresses.
On the Internet, each device connected to the network has a unique IP address that is used to identify and communicate with it. However, IP addresses are difficult to remember and can change frequently. This is where DNS comes into play, providing a domain name system that is easy to remember and remains constant.
DNS works like an Internet phone book, converting domain names into IP addresses. When you type a domain name into a browser, your computer sends a query to the DNS server to obtain the corresponding IP address. The DNS server then responds with the IP address of the destination server, allowing communication between the devices to occur.
Furthermore, DNS is also responsible for storing and updating information about domain names and their corresponding IP addresses in a distributed network of DNS servers, ensuring that the process of translating domain names into IP addresses is fast and efficient.
What is DNS Tunneling?
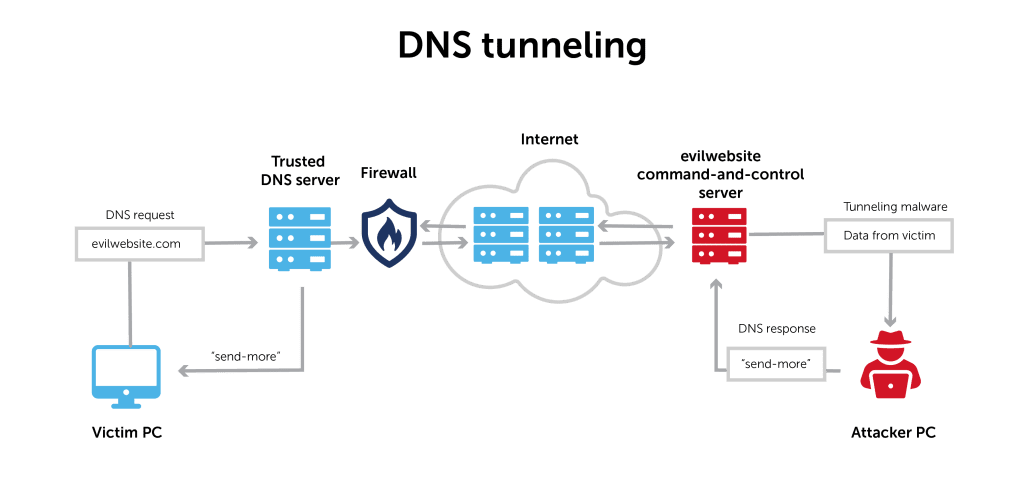
DNS tunneling is a method used to send non-DNS traffic through DNS queries. This is done by encapsulating non-DNS traffic into DNS queries and sending them to a DNS server that is capable of extracting the encapsulated traffic and delivering it to its final destination.
DNS tunneling is commonly used to bypass firewall restrictions or to hide network traffic from detection. For example, DNS tunneling can be used to send VoIP or streaming video traffic through DNS queries, bypassing firewall policies that block this type of traffic.
While DNS tunneling can be useful in some circumstances, it can also be used by cybercriminals to hide malicious activity, such as stealing confidential information or sending spam. For this reason, DNS tunneling is often detected and blocked by security measures such as next-generation firewalls and threat detection solutions.
It’s important to note that DNS tunneling is not a best practice and can have security and performance implications. Network administrators must monitor and block DNS tunneling in order to ensure network integrity and security.
The bad side of DNS
Domain name system (DNS) tunneling is a widespread threat that allows hackers to obtain data inside and outside a company’s internal network while bypassing most firewalls. The domain name system translates numeric Internet Protocol addresses that browsers can use to load web pages – threat actors use tunneling to exploit this process and steal data by hiding it in DNS traffic.
Most DNS attacks focus on spoofing or misdirection, where an attacker provides false information to DNS servers or convinces other systems to query a hostile DNS server instead of a legitimate one. But DNS tunneling essentially smuggles hostile traffic through DNS ports, which makes these attacks difficult to detect and mitigate.
“Attacks that exploit weaknesses in DNS can direct other systems to connect to or trust hostile systems by mistake, all without exploiting conventional vulnerabilities such as missing patches or misconfigurations,” says Jacob Ansari, PCI practice leader at global security firm audit, tax and consultancy Mazars.
Why is DNS a target?
Most DNS attacks arise because the original DNS protocol, dating from the early days of the internet, did not have security functions such as authenticity or integrity. This could give cybercriminals a channel to abuse necessary network services like DNS to exfiltrate data rather than stealing it directly from a network, says Tim Shimeall, a senior technical staff member at the CERT network situational awareness group. from the Carnegie Mellon Software Engineering Institute.
“This abuse is difficult to detect because it is mixed in with the expected and necessary uses of these services – the hide-in-the-crowd approach,” he says. “By applying network monitoring tools and creating familiarity with expected and necessary uses, the challenge of detecting abuse becomes more viable.”
Here are four strategies for identifying and reducing the risk of DNS tunneling:
Combine technical and human solutions
Organizations should look for human and technical solutions to address DNS tunneling, says Terrence O’Connor, assistant professor of engineering and computer science and chair of the cybersecurity program at the Florida Institute of Technology. From a personal perspective, organizations can establish internal, proactive threat-hunting groups.
These groups can improve threat detection and response times by analyzing network traffic logs to identify anomalies or developing signatures based on historical attacks and tools. Additionally, the group can inform network defenders about emerging attack technologies and how they uniquely leverage DNS for malicious purposes.
From a technical perspective, companies can enable security mechanisms that prevent DNS tunneling. For example, organizations can employ DNS Security Extensions (DNSSEC), a security mechanism that requires cryptographic validation of DNS messages, says O’Connor. “While no approach is perfect, the combination of human and technical solutions can largely defeat most DNS tunneling attack approaches.”
Best Defense:
The best approach is a defense-in-depth solution that combines technical aspects with upskilling a security team so they can perform manual analysis if the tools generate any alerts, says David Maynor, director of Cybrary’s threat intelligence group.
“To identify DNS tunneling, organizations must implement tools that provide deep packet inspection and can visualize and analyze DNS packets,” he says. “The rules can then be applied to detect fields that violate the comment request standard.”
Another method is anomaly-based network analysis with which network flow is analyzed for abnormal behavior, Maynor says. For example, a workstation suddenly sending DNS traffic off the network to seemingly random DNS servers would be a huge red flag. Security teams can then respond to alerts generated by the tools about these issues.
Monitor internet activities
The DNS service is a perfect choice and target for attackers due to the sensitivity of this service, so it is important for organizations to rigorously monitor and alert their DNS services for unusual activity, says Izzat Alsmadi, associate professor in the Department of Computing and Cybersecurity at Texas A&M University-San Antonio.
One way to do this is to actively monitor Internet activity and block IP addresses known to create such problems, says Alsmadi. “This is a general blacklisting approach, but it is often difficult to accommodate all possible attackers, so it is important to include rules that alert to strange or unusual DNS queries.”
Protecting local clients and ensuring users know to avoid phishing campaigns is also important, as most DNS attacks begin by exploiting a trusted local client or computer, says Alsmadi.
Dan Petkevich, founder and CEO of Fair Square Medicare, says his company uses technology to help seniors find the insurance that best meets their health needs. Due to the high level of personal data involved in the business, Fair Square Medicare is sensitive to DNS tunneling risks. He says that one of the most practical methods for avoiding DNS tunneling is to continually monitor the type of traffic that frequents a company’s system.
“This allows you to detect any suspicious activity early on and block its access to the network before damage is done,” says Petkevich. “When I’m searching the web, I typically use sites with HTTPS over HTTP protocols because they are more secure against these attacks. As a business owner, it is crucial that your web developer includes the HTTPS protocol on your website. Nowadays, even Google is aware of the high risk of DNS tunneling and therefore tends to warn internet users if a website is not well equipped to protect their data.”
Ensure third parties correct incorrect settings on their DNS servers
Some DNS attacks involve denial of service (DoS) attacks or distributed denial of service (DDoS) attacks, in which an attacker sends a large number of hostile DNS queries that can overload the DNS infrastructure and cause Internet outages in the victim organizations, says Ansari.
Some of these attacks use third-party DNS servers to respond to victim organizations’ DNS servers. “The solution to these attacks is to have the other parties correct incorrect settings on their DNS servers. As such, this can be difficult to resolve if these parties do not cooperate or are bribed by the attacker,” says Ansari. “If third parties do not adhere to good DNS security practices, factor this into contract renewal negotiations and third-party risk management efforts.”
Employee training
Because of the many legitimate uses of DNS, it’s difficult to tell whether data fields in requests and responses are valid, according to Maynor. “Attackers capitalize on the complexity and trusted and necessary nature of DNS by creating their own seemingly real DNS traffic with data in the fields,” he says. “This gives an attacker inside a network the ability to exfiltrate data in a way that appears legitimate to the casual user.”
Consequently, to keep systems safe from DNS tunneling, companies should conduct regular employee training programs on phishing, malware, and DNS tunneling attacks, says Ihab Shraim, chief technology officer at CSC Digital Brand Services. Employees who recognize and prevent social engineering attacks can prevent DNS tunneling attempts.
Organizations should also train cybersecurity teams to recognize DNS traffic patterns that are not typical. Implementing machine learning techniques into DNS traffic can help security teams detect anomalies in patterns. You can also hire an IT company to work on your network security.